Introduction
Understanding the complexities of HTTP proxies is crucial for anyone aiming to elevate their online experience in 2025. These intermediaries not only enhance privacy and security but also improve performance and access control. Yet, many users are unaware of the full potential and the implementation challenges that come with setting up an HTTP proxy server.
What steps should you take to effectively harness these benefits? How can you troubleshoot the common issues that arise during the process? By addressing these questions, you can unlock the true power of HTTP proxies and navigate the digital landscape with confidence.
Understand HTTP Proxy Basics
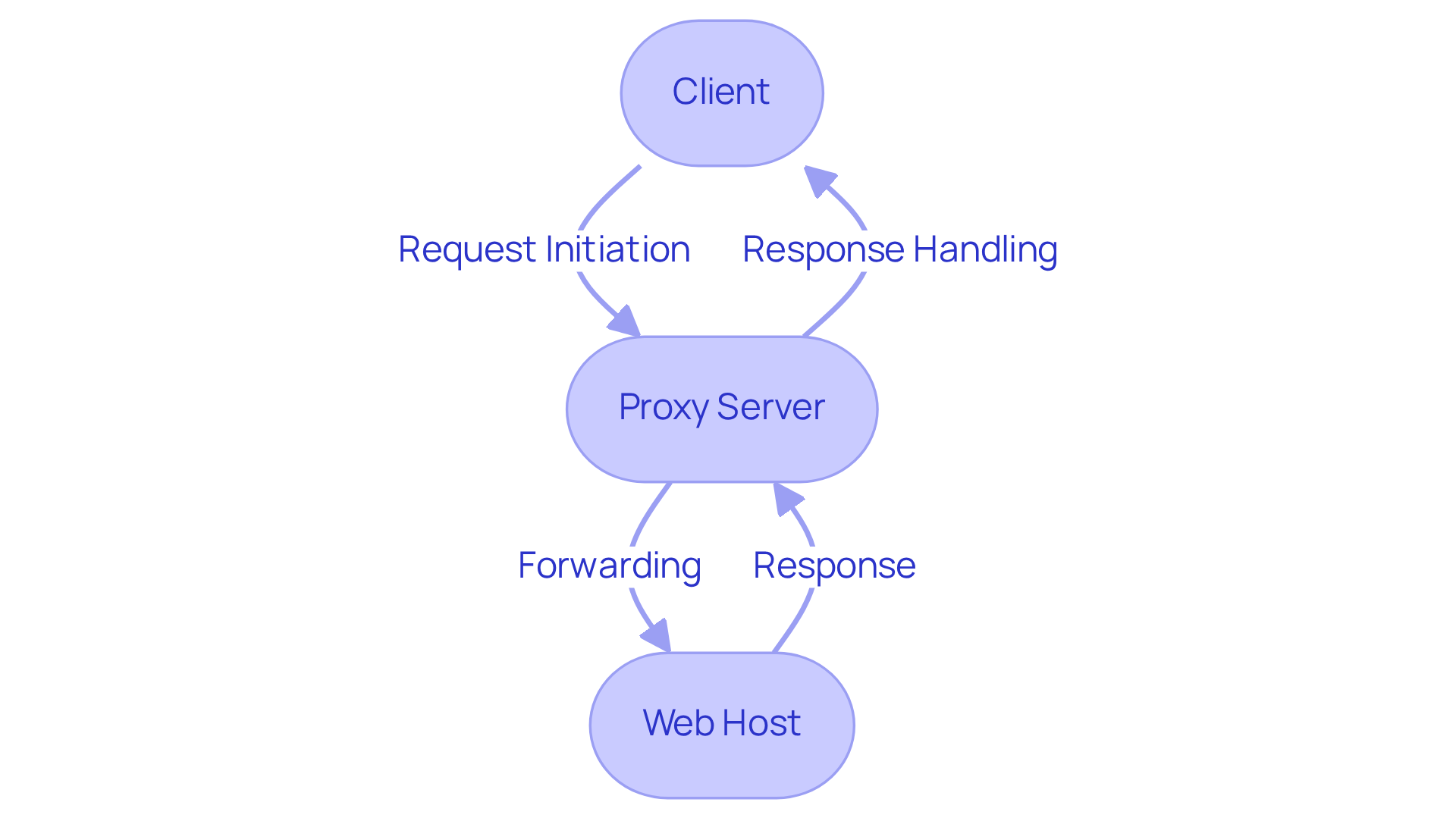
An HTTP intermediary plays a crucial role between a client - like your web browser - and a web host. When you request access to a website, that request first reaches the intermediary, which then forwards it to the target system. The server's reply is sent back to the intermediary, which subsequently delivers it to you. This process not only enhances privacy but also boosts performance and enables content filtering. Understanding this flow is vital for effectively implementing a web proxy.
Key Components of an HTTP Proxy:
- Client: The device or application making the request.
- Proxy Server: The intermediary that processes requests and responses.
- Web Host: The destination machine providing the requested content.
How It Works:
- Request Initiation: The client sends a request to the intermediary host.
- Forwarding: The intermediary system sends the request to the web host.
- Response Handling: The web server transmits the response back to the intermediary, which then forwards it to the client.
This fundamental understanding is essential as it lays the groundwork for exploring the advantages and applications of web intermediaries in the sections to follow.
Explore Benefits of HTTP Proxy in 2025
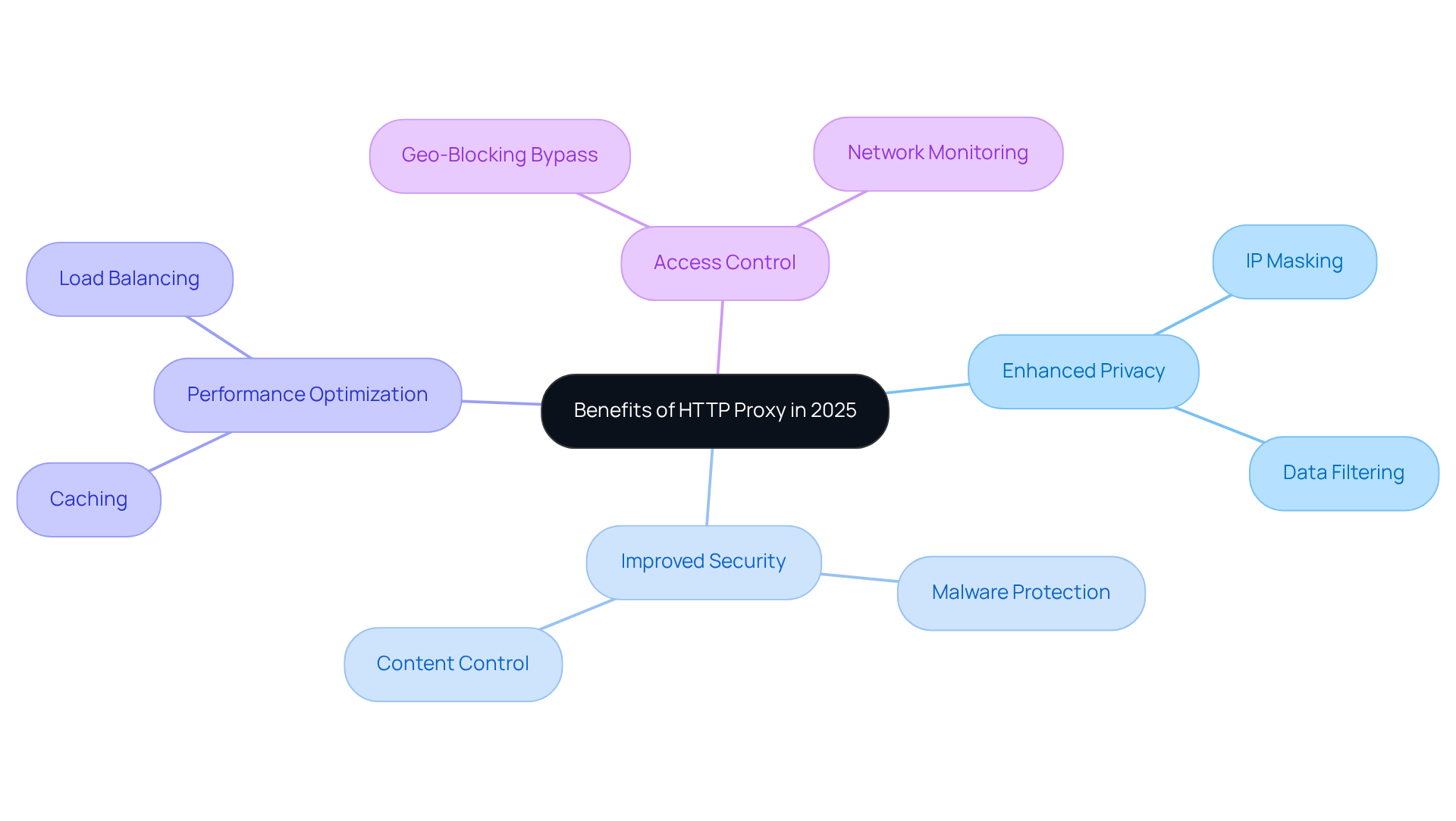
In 2025, http proxy 2025 offers a wealth of advantages that significantly enhance online activities for both individuals and businesses. Let’s explore some of the key benefits:
Enhanced Privacy
- IP Masking: Proxies effectively conceal your real IP address, ensuring anonymity while you browse. This is crucial in a digital landscape where privacy is paramount.
- Data Filtering: They can filter out sensitive information from requests, safeguarding user privacy and preventing data leaks.
Improved Security
- Malware Protection: Proxies play a vital role in blocking access to malicious sites, thereby reducing the risk of cyber threats that can compromise sensitive information.
- Content Control: Organizations can enforce policies to restrict access to inappropriate content, creating a safer online environment for employees.
Performance Optimization
- Caching: Proxies cache frequently accessed content, which significantly speeds up load times for users. This efficiency can enhance user satisfaction and productivity.
- Load Balancing: They distribute traffic evenly across servers, improving overall performance and ensuring that no single server becomes overwhelmed.
Access Control
- Geo-Blocking Bypass: Proxies enable users to access content that may be restricted in their region, broadening the scope of available information and resources.
- Network Monitoring: Organizations can effectively monitor and control employee internet usage, ensuring compliance with company policies.
These advantages clearly illustrate why utilizing a web gateway is a strategic decision for enhancing both individual and organizational online experiences. Are you ready to leverage these benefits for your online activities?
Implement HTTP Proxy: Step-by-Step Guide
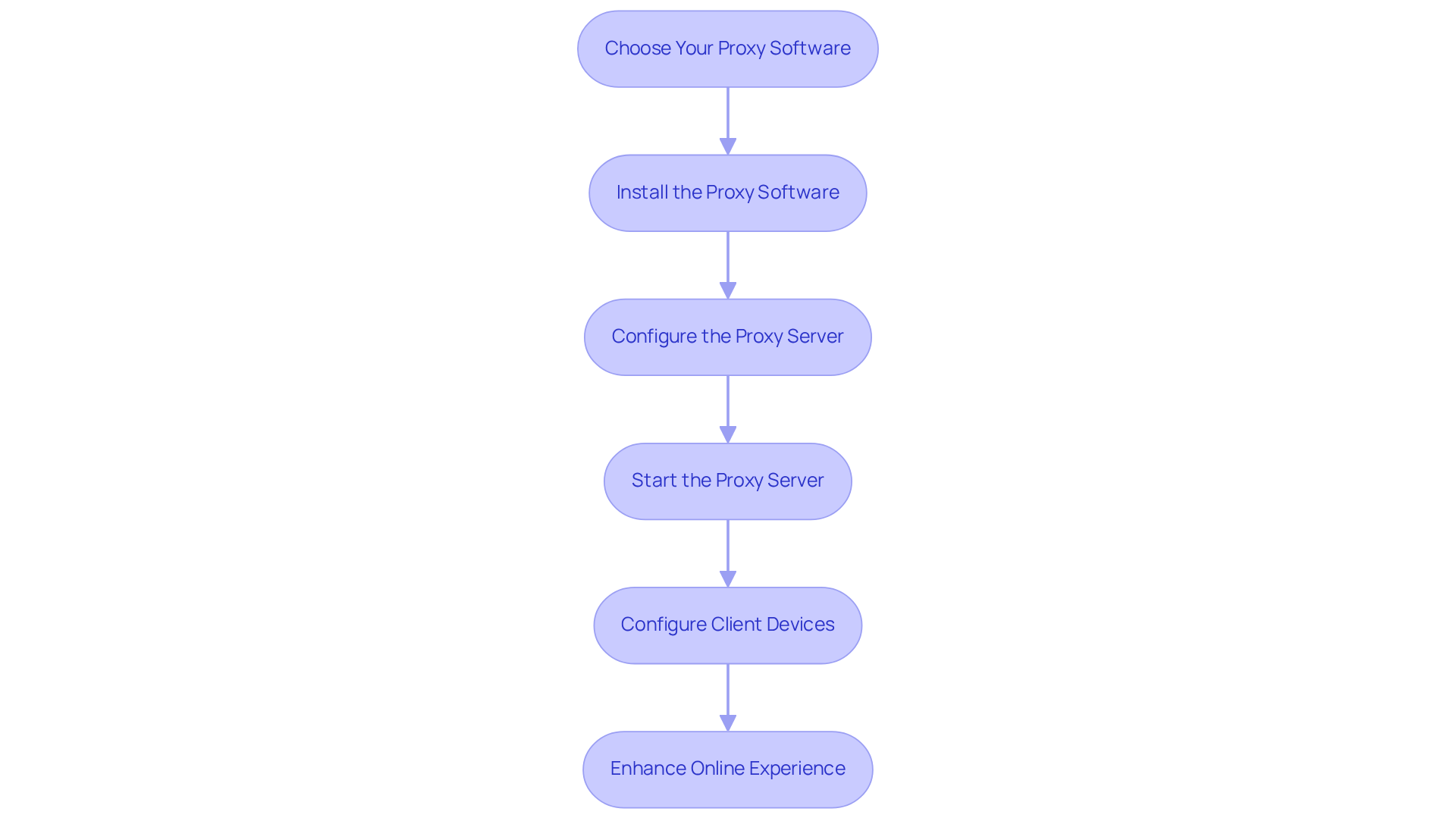
Setting up a web intermediary is a multi-stage process that can significantly enhance your online activities. Follow this guide to establish your own HTTP proxy server with confidence:
Step 1: Choose Your Proxy Software
Begin by selecting a reliable proxy server software. Popular options include Squid, Nginx, and Apache. For this guide, we will focus on Squid as our example.
Step 2: Install the Proxy Software
- For Linux: Utilize the package manager to install Squid:
sudo apt-get install squid - For Windows: Download the installer from the official Squid website and follow the provided installation instructions.
Step 3: Configure the Proxy Server
- Locate the configuration file, typically found at
/etc/squid/squid.conffor Linux or within the installation directory for Windows. - Open the file in a text editor and modify the following settings:
- http_port: Specify the port number for the proxy (default is 3128).
- acl: Define access control lists to specify who can utilize the intermediary.
- http_access: Allow or deny access based on the defined ACLs.
Step 4: Start the Proxy Server
- For Linux: Execute the following command:
sudo systemctl start squid - For Windows: Start the Squid service from the Services management console.
Step 5: Configure Client Devices
- On the client device, navigate to the network settings.
- Enter the intermediary's IP address and port number in the settings section.
- Save the changes and test the connection by accessing a website.
By following these steps, you will effectively establish a web intermediary that enhances your online experience. Are you ready to take control of your internet traffic?
Troubleshoot Common HTTP Proxy Issues
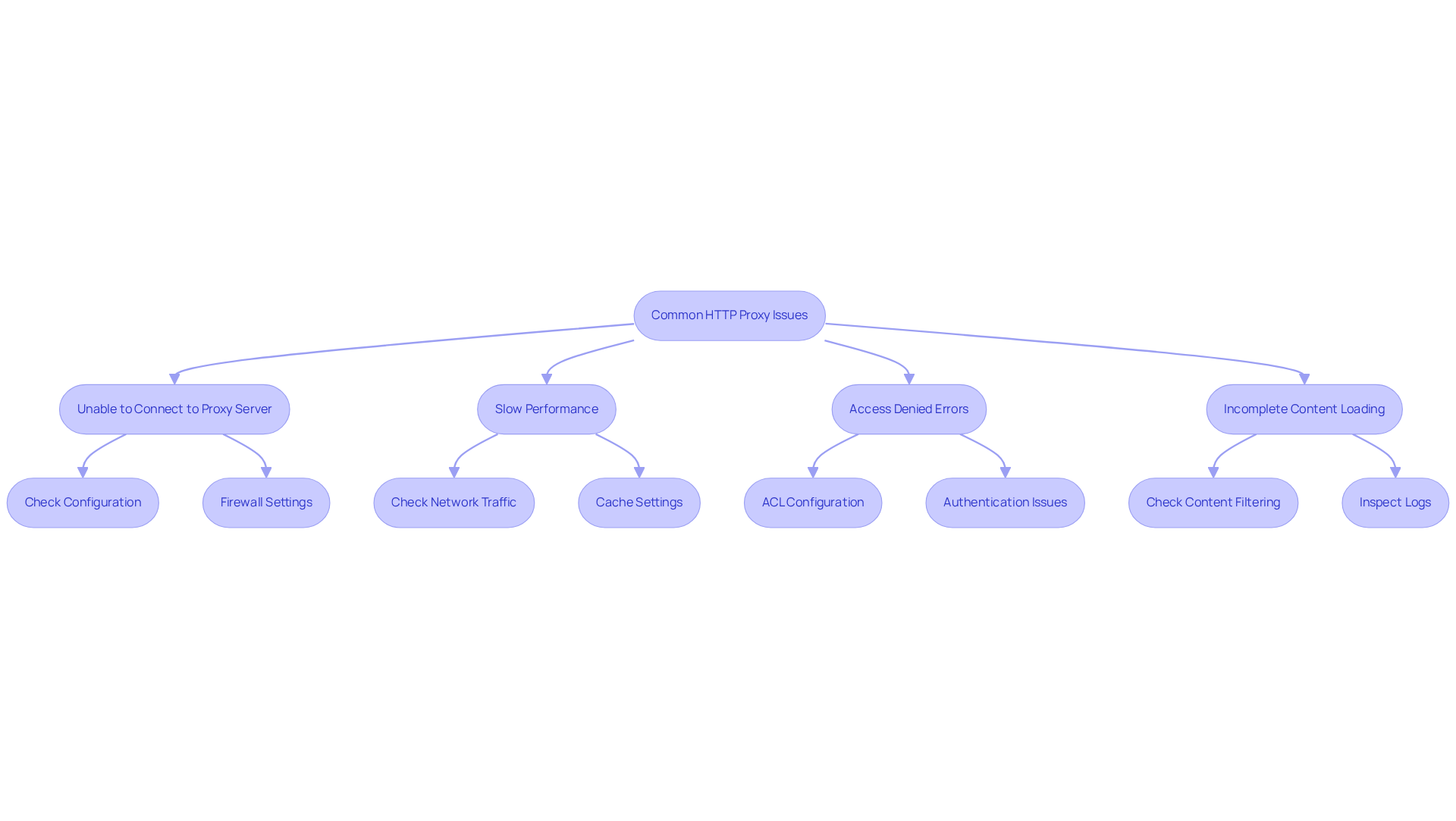
After implementing your HTTP intermediary, you might face several common issues. Here are effective troubleshooting steps to resolve them:
Issue 1: Unable to Connect to Proxy Server
- Check Configuration: Ensure that the proxy settings on the client device match the server's IP address and port.
- Firewall Settings: Verify that the firewall isn’t blocking the port for the intermediary; this is a frequent cause of connection failures.
Issue 2: Slow Performance
- Check Network Traffic: High traffic can significantly slow down the proxy. Statistics show that improper configuration and network congestion account for about 70% of intermediary connection failures. Monitor usage patterns and consider implementing load balancing to distribute the load effectively.
- Cache Settings: Make sure caching is enabled and configured correctly, as proper caching can enhance response times and reduce latency.
Issue 3: Access Denied Errors
- ACL Configuration: Review the access control lists in the proxy configuration to confirm that the client IP is permitted access. Misconfigured ACLs often lead to entry issues.
- Authentication Issues: If authentication is required, double-check that the correct credentials are being used; incorrect logins can result in access denials.
Issue 4: Incomplete Content Loading
- Check Content Filtering: Ensure that the proxy isn’t inadvertently blocking legitimate content due to overly restrictive filtering rules. This can lead to incomplete page loads.
- Inspect Logs: Review the intermediary logs for any errors or warnings that may indicate the source of the problem. Logs can provide critical insights into connection issues.
In a recent case study, a gaming company utilized advanced intermediary solutions to automate player experience tickets, significantly reducing the number of unresolved issues related to connection methods. By following these troubleshooting steps, you can effectively manage and maintain your http proxy 2025 server, ensuring it operates smoothly and efficiently. Incorporating these practices is essential, especially considering that a significant percentage of proxy connection failures stem from configuration and network issues.
Conclusion
Implementing an HTTP proxy in 2025 is not just a technical choice; it’s a strategic move to enhance your online experience. With improved privacy, security, and performance, an HTTP proxy serves as a vital tool in today’s digital landscape. This guide has outlined the essential components and workings of an HTTP proxy, illustrating its role as a crucial intermediary between clients and web hosts. By grasping this framework, users can effectively leverage the advantages of a web proxy to optimize their online activities.
The article has delved into the numerous benefits of using an HTTP proxy. Enhanced privacy through IP masking, increased security by blocking malicious sites, and performance optimization via caching and load balancing are just a few highlights. Furthermore, a step-by-step guide for setting up a proxy server was provided, addressing common issues that may arise during implementation. These insights collectively underscore the strategic importance of HTTP proxies in our ever-evolving digital environment.
As the online landscape continues to shift, harnessing the capabilities of an HTTP proxy becomes increasingly essential. By adopting these practices and troubleshooting strategies, users can take control of their internet traffic, ensuring a safer and more efficient browsing experience. Embracing these tools not only enhances individual online activities but also supports businesses in maintaining compliance and safeguarding sensitive information. Are you ready to take the next step in optimizing your online presence?
Frequently Asked Questions
What is the role of an HTTP proxy?
An HTTP proxy acts as an intermediary between a client, such as a web browser, and a web host. It processes requests from the client, forwards them to the target system, and then delivers the server's response back to the client.
What are the key components of an HTTP proxy?
The key components of an HTTP proxy include the client (the device or application making the request), the proxy server (the intermediary that processes requests and responses), and the web host (the destination machine providing the requested content.)
How does the HTTP proxy process work?
The process works in three main steps: 1. Request Initiation: The client sends a request to the intermediary host. 2. Forwarding: The intermediary system sends the request to the web host. 3. Response Handling: The web server transmits the response back to the intermediary, which then forwards it to the client.
What are the benefits of using an HTTP proxy?
Using an HTTP proxy enhances privacy, boosts performance, and enables content filtering.
Why is it important to understand how an HTTP proxy works?
Understanding how an HTTP proxy works is essential as it lays the groundwork for exploring the advantages and applications of web intermediaries.




